
The Financial Benefits of Shift-Left Security
DevSecOps engineers can help businesses mitigate security risks and minimize vulnerabilities in software development. Adopting Shift-Left security, which addresses security issues earlier in the development process, can reduce the cost of fixing vulnerabilities and prevent costly breaches. In this article, we will explore what DevSecOps is, why organizations need a DevSecOps engineer, and the benefits of Shift-Left security.
11 min read
In this Article:
- The importance of having a DevSecOps engineer on board
- How Shift-Left Security should be integrated into the software development cycle
- A breakdown of the financial benefits of implementing Shift-Left security
In today’s digital landscape, security is a top concern for organizations of all sizes, and with the rise of cyber threats, companies must prioritize security in their software development processes. This is where a DevSecOps engineer comes in. DevSecOps is an approach to software development that integrates security practices into the entire software development lifecycle. A DevSecOps engineer is responsible for ensuring that security is considered at every stage of the development process. A DevSecOps engineer is also crucial in applying a Shift-Left security approach. In this article, we will explore why organizations need a DevSecOps engineer onboard, and the benefits that Shift-Left security can bring to a software development process.
Why you need a DevSecOps engineer onboard
DevSecOps is an approach that combines development, security, and operations to create a more efficient and secure software development process. DevSecOps engineers are professionals who focus on integrating security into the DevOps software development process from the start. They work with development and operations teams to design and implement secure architectures for software systems. Their role involves implementing the steps of Shift-Left security, which emphasizes the importance of identifying and addressing security issues as early as possible in the development process.
DevSecOps engineers also play a critical role in promoting a culture of security within development teams. They educate developers and other stakeholders about the importance of security and encourage a proactive approach to identifying and addressing potential vulnerabilities. Compliance with regulatory and industry security standards, such as HIPAA, PCI-DSS, and ISO 27001, is also essential to DevSecOps engineers, who ensure that the system is compliant and monitored to track compliance status.
In the event of a security incident, the DevSecOps engineer coordinates with the incident response team to identify and contain the issue. They also work to identify the root cause of the incident and implement remediation plans to prevent future incidents.
Shift-Left security is an essential component of DevSecOps, and DevSecOps engineers play a key role in implementing this approach. By integrating security testing and analysis into the early stages of the development process, they can help ensure that software is secure, reliable, and efficient, while reducing the risk of costly security vulnerabilities.
What is Shift-Left security about?
Shift-Left security is an approach to software development that puts security at the forefront. This method emphasizes integrating security practices right from the start of the development process. Traditionally, security was addressed late in the cycle, with testing and analysis taking place only after software development. But Shift-Left security changes the rules by detecting and addressing security issues as early as possible in the development process, thereby minimizing the risk of security breaches and vulnerabilities.
The term “Shift-Left” refers to the idea of moving security testing and analysis earlier in the development process. This approach encourages developers to consider security issues from the beginning of the development process, rather than waiting until the end.
The software development process typically involves seven standard steps, starting with Requirements Analysis, where the requirements for the software are gathered and analyzed. The next phase is Design, where the software architecture and design are created based on the requirements identified in the previous phase. Implementation and Coding follow, where the software is developed based on the specifications created in the design phase. Once the software is developed, Testing takes place to ensure that it meets the requirements and works as intended. After testing is complete, the software is Deployed to the production environment, and the final phase is Maintenance, which involves ongoing servicing of the software, including bug fixes and updates.
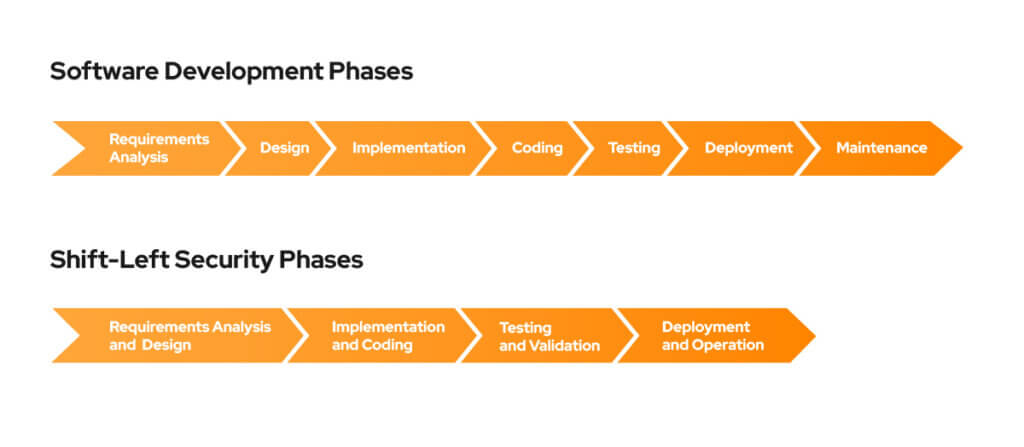
As previously mentioned, in traditional software development, security is often addressed at the end, with security testing and analysis taking place only after the software has been developed. However, Shift-Left security seeks to address security issues earlier in the development process by taking steps in parallel during the software development process. We can simplify these steps as follows:
Requirements Analysis and Design: The first step in Shift-Left security is to identify the security requirements for the application or software being developed. This includes defining the threat model, outlining the security goals, and identifying the security controls that need to be implemented.
Implementation and Coding: Once the security requirements have been identified, the next step is to integrate security into the development process. This can be done by using secure coding practices, conducting code reviews, and using automated security testing tools.
Testing and Validation: In Shift-Left security, security testing is conducted throughout the development process. This includes unit testing, integration testing, and system testing. Automated testing tools can be used to identify security vulnerabilities and provide feedback to developers.
Deployment and Operation: As vulnerabilities are identified, security controls should be implemented to mitigate the risk. This includes implementing security policies, hardening the system, and using security frameworks and libraries. Even after the software has been deployed, Shift-Left security requires ongoing monitoring and maintenance. This includes monitoring the system for security events, patching vulnerabilities, and conducting regular security assessments.
You may have noticed that the phases of Shift-Left security mirror those of the software development cycle, but with a different focus and goal. This is no coincidence, as Shift-Left security is intended to complement the development process seamlessly. By keeping this harmony, organizations can detect and remediate security weaknesses at each stage, lowering the risk of cyber attacks and strengthening the security posture of the entire system.
The financial benefits of DevSecOps implementing Shift-Left practices
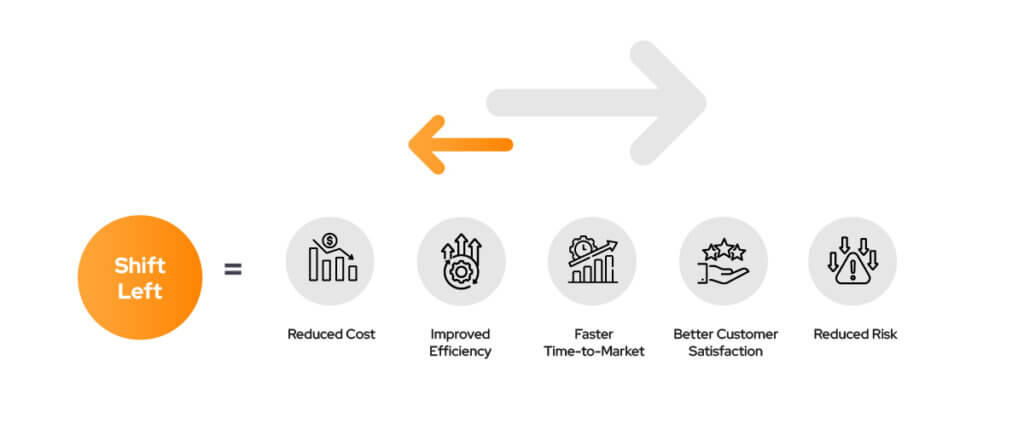
In addition to the obvious advantages of a secure and safe software development process, there are also financial benefits that can boost an organization’s bottom line. Ultimately, investing in DevSecOps and Shift-Left security can pay off in both the short and long term for organizations, with the following examples:
Cost Reduction: Identifying vulnerabilities earlier in the development cycle means that fewer resources will be required to fix them, resulting in significant cost savings.
Efficiency Boost: By catching and fixing vulnerabilities early on, developers can avoid more complex and costly issues down the road, leading to increased efficiency and productivity.
Faster Time-to-Market: In today’s fast-paced market, speed is everything. By utilizing Shift-Left security, businesses can speed up the development process and get products to market faster, leading to increased revenue and profitability.
Improved Customer Satisfaction: Security is a top priority for consumers, and businesses that take it seriously gain their trust and loyalty. By implementing Shift-Left security, businesses can demonstrate their commitment to security, leading to better customer satisfaction and retention.
Reduced Risk: Security breaches can have devastating consequences, both financially and in terms of reputational damage. Implementing Shift-Left security helps reduce the risk of breaches, providing long-term financial benefits for businesses. Don’t ignore the importance of Shift-Left security – it can make all the difference for your business’s success.
Secured software development ensures a safe market position
By adopting a Shift-Left security approach, companies can save money in the long run, with improved efficiency, faster time-to-market, and increased customer satisfaction. In addition, a secure software development process can also help organizations avoid costly security breaches and the resulting reputational damage. Therefore, organizations must prioritize the need for a DevSecOps engineer to perform Shift-Left security if they want to succeed in the highly competitive market. A DevSecOps engineer’s job is crucial in providing reliable, efficient, and trustworthy software that meets both business requirements and customer expectations.
As software continues to play a crucial role in managing operations and customer interactions, ensuring its security is no longer simply an option, but an absolute necessity. By making security a top priority in the software development process, organizations can solidify their reputation as a trusted and secure entity. And in today’s business world, being known for reliability and security is a key ingredient for achieving success.




